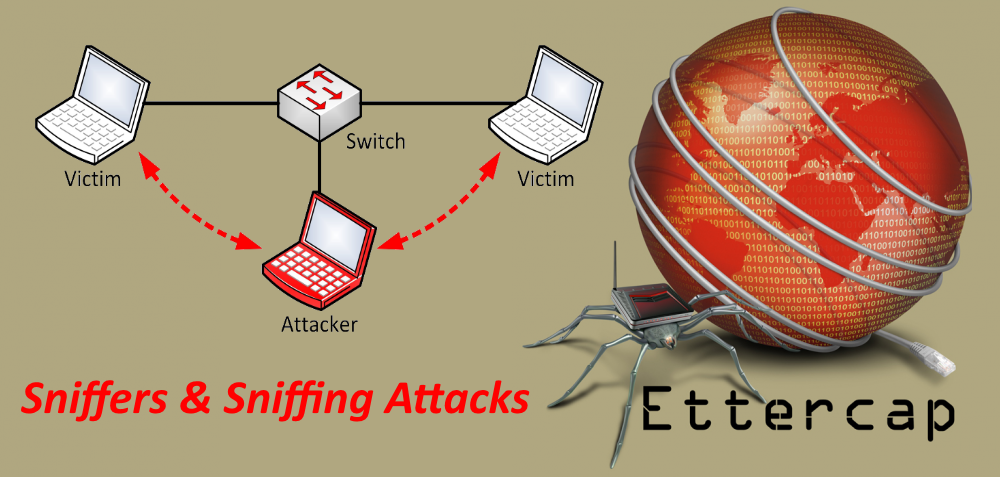
A sniffer is an application that captures network packets. Sniffers are known as network protocol analyzers. While protocol analyzers are actually network troubleshooting tools used by software development companies in india, they are also used by hackers for hacking network. If the network packets are not encoded, the data inside the network packet can be recited using a sniffer. Sniffing refers to the process used by attackers to capture network traffic by a sniffer. Once the packet is seized using a sniffer, the contents of packets can be examined. Sniffers are used by hackers to capture delicate network information, such as account information, passwords etc.
Different types of attacks are as following:
1.1 A LAN sniff
A sniffer arranged on an internal LAN can scan the whole IP range lasciviously. This helps in providing more details such as live hosts, server inventory, open ports etc. Once a list of open ports is collected, a port-specific vulnerability attack is possible.
1.2 A protocol sniff
This technique involves sniffing data associated to the network protocols being used. First, a list of protocols is formed based on the captured data. This is further isolated to create special sniffers for each attack. For example, in a system sniff capture, if the ICMP protocol is not seen, it is expected to be blocked. However, if UDP packets are seen, a distinct UDP sniffer is started to capture and decipher Telnet, PPP, DNS and other connected application details.
1.3 An ARP sniff
In this popular method, the hacker captures a lot of data in order to create a map of IP addresses and the associated MAC addresses. Such a map is further used to create ARP poisoning attacks, packet-spoofing attacks, or to dig into router-based vulnerabilities.
1.4 TCP session stealing
This method is a simple form of sniffing, in which a network interface in licentious mode captures traffic between a source and a destination IP address. Details such asservice types,port numbers, TCP sequence numbers and the data itself are of interest to hackers. Upon capturing packets, advanced hackers can create fictitious TCP sessions to fool the source and destination, and be the man in the middle to take over the TCP session.
1.5 Application-level sniffing
From the data packets sniffed and captured, a few complicated application details are found out for information burglary or to create further attacks. As an example, the capture file can be analyzed to perform SQL query analysis, OS fingerprinting, reveal application-specific TCP port data information, etc. In alternative approach, generating a mere list of applications running on a server is decent enough to plan an application-specific attack on it.
1.6 Web password sniffing
As the name suggests, HTTP sessions are stolen and analyzed for user ID and password stealing. While the Secure Socket Layers (SSL) are combined for securing HTTP sessions on the network, there are many internal websites that still use standard but less protected encryption. It is easy to capture Base64 or Base128 packets and run a deciphering agent in contrast to crack the password. In modern sniffers, SSL sessions can also be captured and analyzed for information, though this method is not very simple.
1.7 Detecting sniffers
As mentioned earlier, since sniffers work mutely, it is very difficult to perceive them on a network. There are few tricks that can provide a clue to a likelysniffer presence. There are two ways to detect a sniffer, network-basedand host-based.In host-based detection, you can use small services to detect if the NIC is running in a licentious mode on any host in a network. Since the elementary requirement for a sniffer to work is to put the network interface in “read all” mode, restrictingit can very effectively help shutting down stray sniffers.In case of network-based discovery, anti-sniffer software can be run to sense the presence of specific signature packets. In alternative approach, scripts can be run to check each network host for the occurrence of known processes, sniffers etc. Modernanti-spyware or anti-virus software are proficient of detecting sniffing software and disabling it.
No comments:
Post a Comment